Traditional Linux networking is satisfied for most situations when employed in network switch, router or other network devices. However, it still has some limitations such as the problem of UNIX file permissions, which affects network security. Luckily, Access Control List (ACL) has been developed, which is designed to make a flexible permission mechanism in Linux. Well, what is ACL and how to use it in Linux?
Access Control List Overview
Access Control List is a list that grants or denies permissions to the data, which tries to access services attached to that network hardware such as Gigabit Ethernet switch or router. There are several types of ACLs such as access ACL and the default ACL. The former is the access control list for a specific file or directory and the later can only be associated with a directory.
ACL provides an additional, more flexible permission mechanism for file systems. To be specific, it ensures security by blocking packets that are destined to sensitive areas in the network. Based on the protocols, it also determines the type of traffic to forward. And it is also able to deny certain users or groups access to the Internet while allowing others. What’s more, ACL can block specified traffic, which greatly helps enhance the performance of your network.
How to Use Access Control List in Linux?
Usually, there are mainly four steps for the Access Control List configuration.
Before using ACLs for a file or directory, you should install the acl package.
1.Mount the file system consisting of the file or directory with ACL support. Here is the syntax for you to mount a local ext3 file system.
2.Use the getfacl utility to show a file’s ACL.
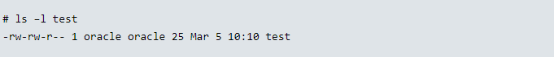
When a file does not have an ACL, it shows the same information as ‘ls –l’, although in a different format.
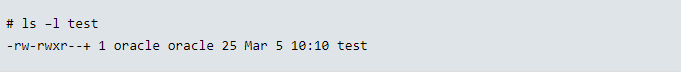
3.Use the setfacl utility to add or modify one or more rules in a file’s ACL.
If a file has an ACL, ‘ls –l’ will display a plus sign (+) following the permission.
1.Use the “-x” option without specifying any permissions to remove rules for a user or group.
2.Use the “-b” option to remove ACL itself.
Add “d:” before the rule and specify a directory instead of a file name. Then the setting is completed.
What Is Linux ACL Mask and Why Does It Exist?
When setting the default ACL in a directory, some users may be confused to see “default:mask” or just “mask”. Actually, the “mask” is a mask setting, which is used to mask out permissions. Except a file owner or an “other” entry, “mask” is the maximum permission granted by access control entries for users and groups. The “default: mask” on a parent directory is also a mask setting, which is applied to things that are created within it.
Conventionally, people use the traditional Unix applications to run “chmod(…,000)”, which is expected to deny all access to a file. However, it fails unless there is a mask and the old “S_IRWXG” permissions map to it. Although having been upgraded several times, traditional Unix scripts still can’t work perfectly without a mask. In ACLS, the mask is also necessary. Without it, setting the file permissions to a entry such as “000” wouldn’t affect any non-owner user or group entries and other users still have access to the object. What’s more, without a mask, other approaches have defects in granting or denying permissions to the data as well.
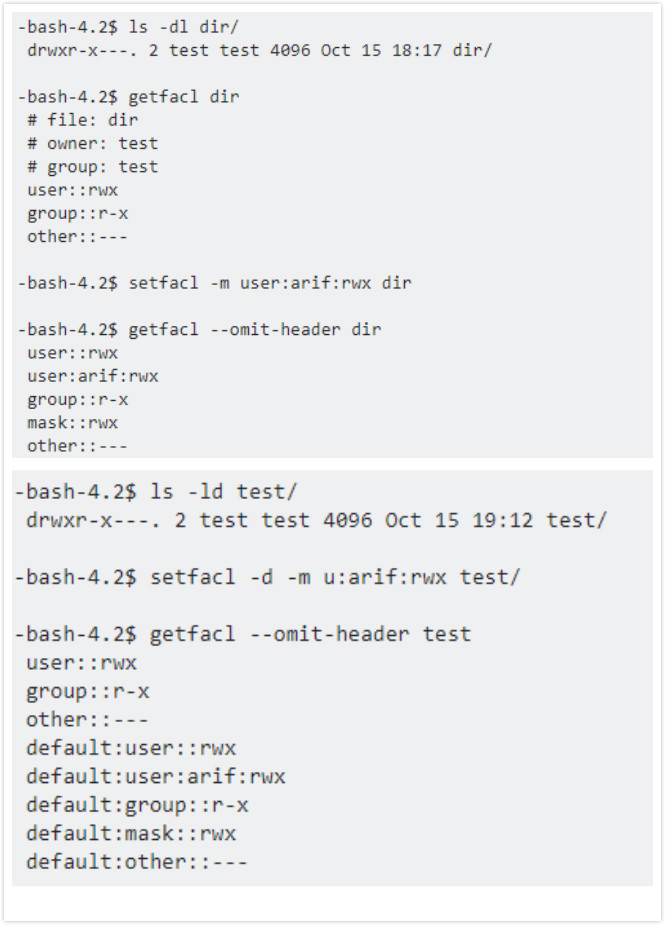
Figure 1: “mask” and “default: mask” scenario
Conclusion
From all the above, you may have a general understanding of Access Control List Linux, Linux ACL Mask and how to use ACL in Linux. The use of ACL in the Linux OS is important to the security of network. Recently, FS has teamed up with Cumulus to provide the N-series open networking switch. These switches are suitable for you to configure ACL, including 10GbE switch, 40GbE switch, 100GbE switch, etc. For more information, please read this news: FS.COM Collaborates with Cumulus Networks to Bring Open Networking Directly to Its 100,000+ Customers.
Related Article:
Network OS Comparison: Open Source OS or Proprietary OS